First Page Design
Site Theme
Google was left hosting such a convincing malvertising ad that there’s a good chance it managed to fool some of the most security-savvy users who came across it.
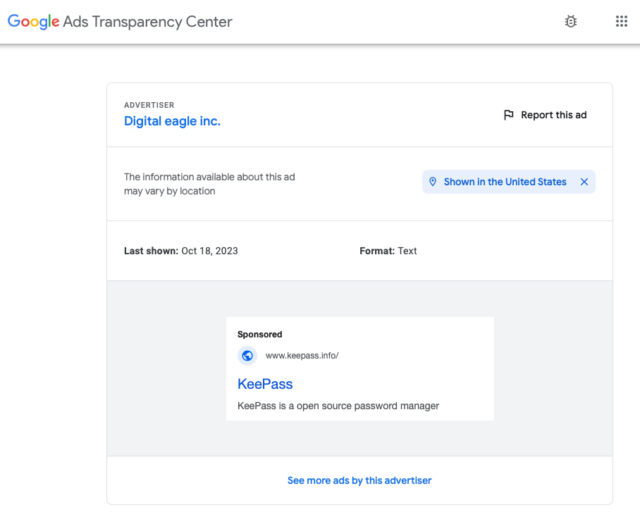
Looking at the ad, which masquerades as a proposal for the open-source password manager Keepass, there’s no way to know it’s fake. After all, it’s Google that lays claim to the classified ads it runs. Which makes the deception even more compelling. Clicking on it displays classified ads to access the ķeepass[. ] information, which, when displayed in an address bar, appears to be the genuine Keeass site.
However, a closer look at the link shows that the site is not genuine. In fact, ķeepass[. ] info, at least when it appears in the address bar, is just a coded way of indicating xn--eepass-vbb[. ] information, which ultimately powers a malware family known as Fake Bat. Combining the ad on Google with an online page with almost the same URL creates almost the best typhoon of deception.
“Users are first duped with Google advertising that looks absolutely legitimate, and then with a similar domain,” Jerome Segura, head of risk intelligence at security vendor Malwarebytes, wrote in an article revealing the scam on Wednesday.
Information from Google’s Ads Transparency Center shows that classified ads have been running since Saturday and made the last impression on Wednesday. The classified ads were paid for through a company called Digital Eagle, which, according to the transparency page, is an advertiser. whose identity has been verified through Google.
In an email sent after this post was published, a Google representative said the company removed the ad in accordance with its terms of service.
The sleight of hand that allowed the deeds of the impostor xn--eepass-vbb[. ] to look like ķeepass[. ] INFO is an encoding formula known as PunyCode. Allows Unicode characters to be rendered in popular ASCII text. If you look closely, it’s easy to spot the small comma-shaped number just below the k. When it appears in an address bar, it’s equally easy to miss the number, especially when the URL is backed by a valid TLS certificate, as is the case here.
There is no surefire way to stumble upon malicious Google classified ads or punycode-encoded URLs. The publication of ķeepass[. ] Info in the five major browsers sends classified ads to the imposter site. When in doubt, users can open a new browser tab and manually enter the URL, but this is not possible if they are durable. Another option is to inspect the TLS certificate to make sure it belongs to the site shown in the address bar.
Join the Ars Orbital Transmission email to receive weekly updates in your inbox. Sign up →
